pfsense
What is pfsense
pfSense is a robust, open-source firewall and router software distribution based on FreeBSD. It provides a powerful and flexible solution for network security management, acting as both a firewall and a router in one. pfSense is designed to handle advanced network configurations with ease, making it a popular choice for businesses, data centers, and home networks alike. Its features include stateful packet inspection, network address translation (NAT), and the ability to manage multiple network interfaces, which gives users granular control over network traffic.
A key feature of pfSense is its user-friendly web interface, which allows users to configure complex firewall rules, set up VPNs, manage bandwidth (traffic shaping), and monitor network activity without needing deep technical knowledge. pfSense supports various VPN protocols like OpenVPN and IPsec, making it ideal for secure remote access. Additionally, it provides support for high availability and load balancing, ensuring that networks remain operational even in the case of hardware failure or high traffic.
pfSense is widely adopted due to its extensive feature set, scalability, and flexibility. While it is open-source, many users rely on it in professional environments for mission-critical operations. It can be installed on dedicated hardware, virtual machines, or used as a pre-built appliance. pfSense’s open architecture also allows for the addition of packages, extending functionality to include things like intrusion detection systems (IDS), content filtering, and anti-virus services, giving users a comprehensive network security and management solution at a fraction of the cost of proprietary systems.


How to install a pfsense
TODO TODO TODO TODO TODO TODO
Install bash
sudo apt install bash
Termomonlogy and Concept
General Networking Terms:
- Firewall: A security device or software that monitors and controls incoming and outgoing network traffic based on security rules.
- Router: A device or software that directs data between computer networks.
- NAT (Network Address Translation): Allows multiple devices on a local network to share a single public IP address by modifying IP addresses as traffic passes through the firewall.
- Packet Filter (pf): The firewall software used by pfSense to filter network traffic based on rules.
- Stateful Packet Inspection (SPI): Monitors active connections and makes firewall decisions based on the state of traffic, not just individual packets.
Network Interfaces and Zones:
- WAN (Wide Area Network): External network connection, typically to the internet, protected by the firewall.
- LAN (Local Area Network): Internal network behind the firewall, managed and protected by pfSense.
- Interfaces: Connections like LAN, WAN, or OPT (optional interfaces) on the firewall that pfSense manages.
Security and Access Control:
- VPN (Virtual Private Network): A secure, encrypted connection over the internet that allows remote access to a network.
- OpenVPN: An open-source VPN protocol used by pfSense for secure connections.
- IPsec (Internet Protocol Security): A protocol suite for securing IP communications through authentication and encryption of packets.
- Intrusion Detection System (IDS): A system that monitors network traffic for suspicious activities or policy violations.
- Intrusion Prevention System (IPS): Extends IDS by actively blocking detected threats.
Traffic Management and Optimization:
- Traffic Shaping: Prioritizing certain types of network traffic to ensure critical applications get the bandwidth they need.
- Load Balancing: Distributing network traffic across multiple connections to prevent overload and improve performance.
- Failover: Automatically switching to a backup connection or device if the primary one fails, ensuring uninterrupted service.
Network and Firewall Configuration:
- Port Forwarding: Directing traffic from a WAN port to a specific device or service on the LAN.
- Firewall Rules: Configurations that determine how pfSense handles network traffic, allowing or blocking traffic based on IP addresses, ports, etc.
- Aliases: Groups of IP addresses, networks, or ports used to simplify firewall rule management.
Advanced Features:
- High Availability (HA): A setup using multiple firewalls to ensure continuous service in case one fails.
- CARP (Common Address Redundancy Protocol): Allows multiple pfSense firewalls to share the same IP address for redundancy and failover.
- Static Route: Manually defined paths for routing traffic to specific networks or devices.
Additional Services and Tools:
- DHCP (Dynamic Host Configuration Protocol): Automatically assigns IP addresses to devices on the LAN.
- DNS Resolver: Resolves domain names to IP addresses, with caching for performance improvements.
- Captive Portal: Requires users to authenticate through a web page before gaining network access (common in public Wi-Fi).
- RADIUS (Remote Authentication Dial-In User Service): A protocol for authenticating users remotely, used with VPNs and captive portals.
Extensions and Add-ons:
- Squid: A proxy server package in pfSense for web content caching and access control.
- Snort/Suricata: IDS/IPS packages that detect and prevent network intrusions and threats.
- Package Manager: Allows for the installation of additional software packages to extend pfSense functionality.
Monitoring and Diagnostics:
- Bandwidth Monitoring: Tools for tracking the amount of data transmitted through network interfaces.
DHCP
DHCP setting
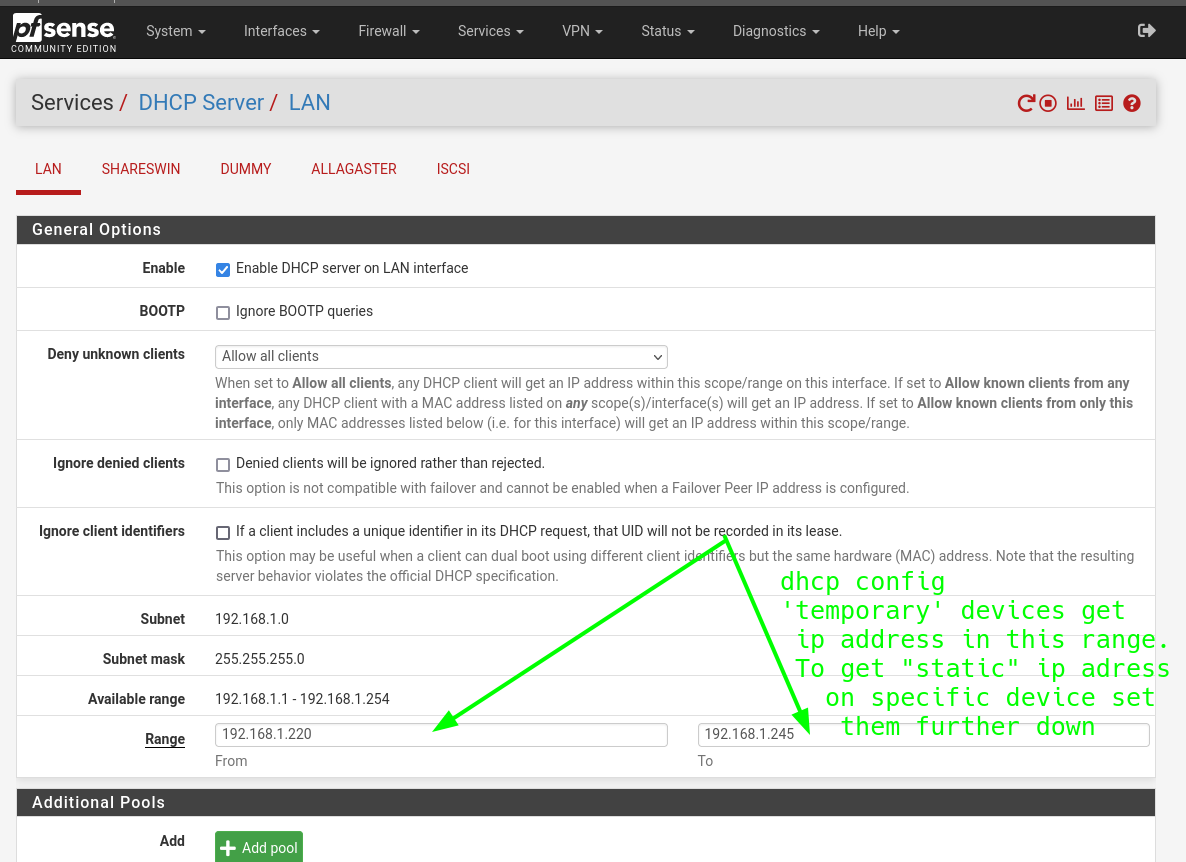
Static ip address based on mac
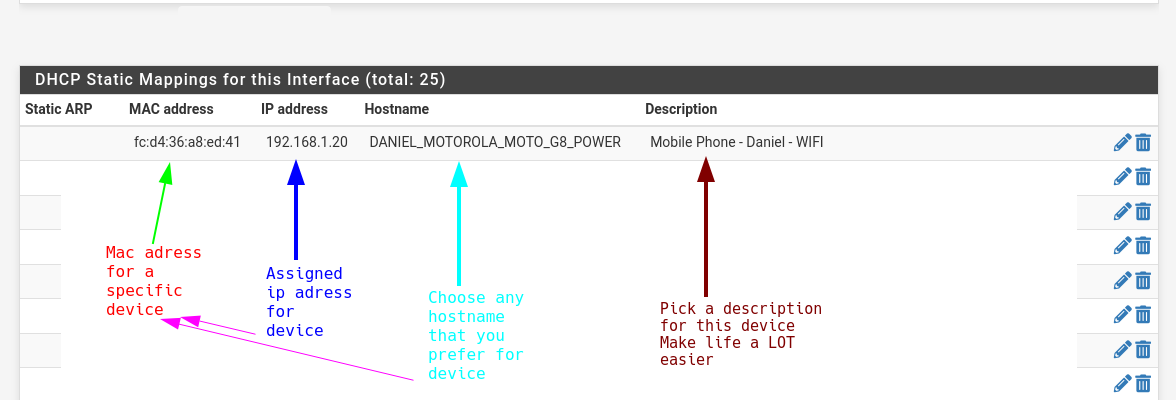
Firewall
- Firewalls control traffic flow between networks based primarily on layer 3 and 4 information (IP and transport)
- Decisions are made by firewall rules
- Rules can perform 3 primary actions on a traffic flow
Pass– allow traffic to pass to destinationReject– drop packets and alert senderBlock– drop packets silently
- The firewall in pfSense is provied by pf (packet filter)
In pfSense, firewall rules can also:
- Mark traffic flows
- For use with other services e.g. traffic shaper
- Log traffic flows
- For network diagnostics
These actions do NOT alter pass/bloc/reject decisions
Basic Operation of the Firewall
- A packet (as part of new connection) arrives at an interface
- Firewall rules are checked against the packet in order
- When a match occurs, the ruls action is taken
- Rule matching stops *
- If no match after all rules are checked, the packet is blocked by default
Block or reject
When in doubt, use block. reject sends a TCP REST of ICMP “Port Unreachable”
- Thous could alert an attacker that there is a firewall at a particular IP address and encourage further probing
- Never use
rejecton a WAN interface
- Never use
rejectwill result in faster failure for application trying to connectrejectmay be useful across private subnet boundaries
Rule Sets
- Each interface has a rule set for
incomingtraffic. Important!- E.g. WAN, LAN, OPTN, WLAN…
- Each VPN virutal interface has a rule set for
incomingtraffic - Each Interface Group has its own rule set
- Floating rules
- NAT port forwarding rules
- Service rules (automatically added, by some package that installed the service, not user configurable)
Rule Ordering
Rules are evaluated in the following order:
- NAT rules
- Service rules
- Floating rules
- Interface Group rules + VPN rules
- Interface rules
Floating rules
- Can match traffic in multiple directions and across mulitple interfaces
- Not usually necessary for most networks
- However they are used heavily by the traffic shaper
- Rules can be overridden by rules in other rule sets
- Floating rules are matched first, but act in a last-match manor
- This behaviour can be overridden by using the quick option
- Quck floating rules act in a first-match manor and will override interface or interface group rules
Firwall Rule Tips
- Order matters
- Rules are checked one at a time in order from the first to last
- Rule checking stops after the first match (except for floating)
- The rule you wanted might never even be checked
- Order rules form most specific to most general
- i.e The more criteria in the rule, the higher it should be
- Ensure the rule is listed on the
incominginterface- Each interface has separate rules
- Ensure no interface group riles also match your traffic
- Interface group rules are matched before interface rules
- Ensure that no quick floating rules also match your traffic
- Rules apply to
connections, NOT individual packets- Adding a new block/reject rule will not sever existing connections
- You can reset the
state tableto correct for this
- By default, an interface has no rules
- All traffic will be blocked by default
- You must explicitly add pass rules to any optional interfaces
- By default, all unmatched traffic flows are blocked
- Known as the whitelist approach
- All traffic must be explicitly allowed
- Useful for WAN connections
- You can add an ‘allow to all’ wildcard rule at the end of the interface rule set to invert this behaviour
- Known as the blacklist approach
- All traffic must be explicitly blocked
- Useful for LAN interfaces
Firewall Rules
Allow to All
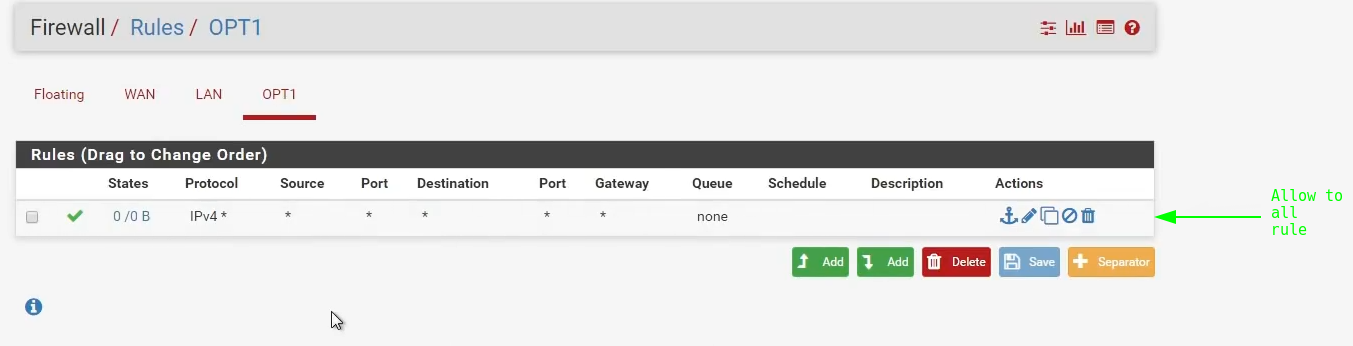
Deny all - Not setting a rule at all, the default in pfsense
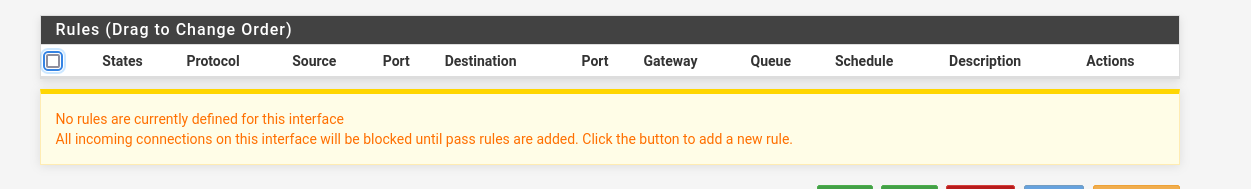
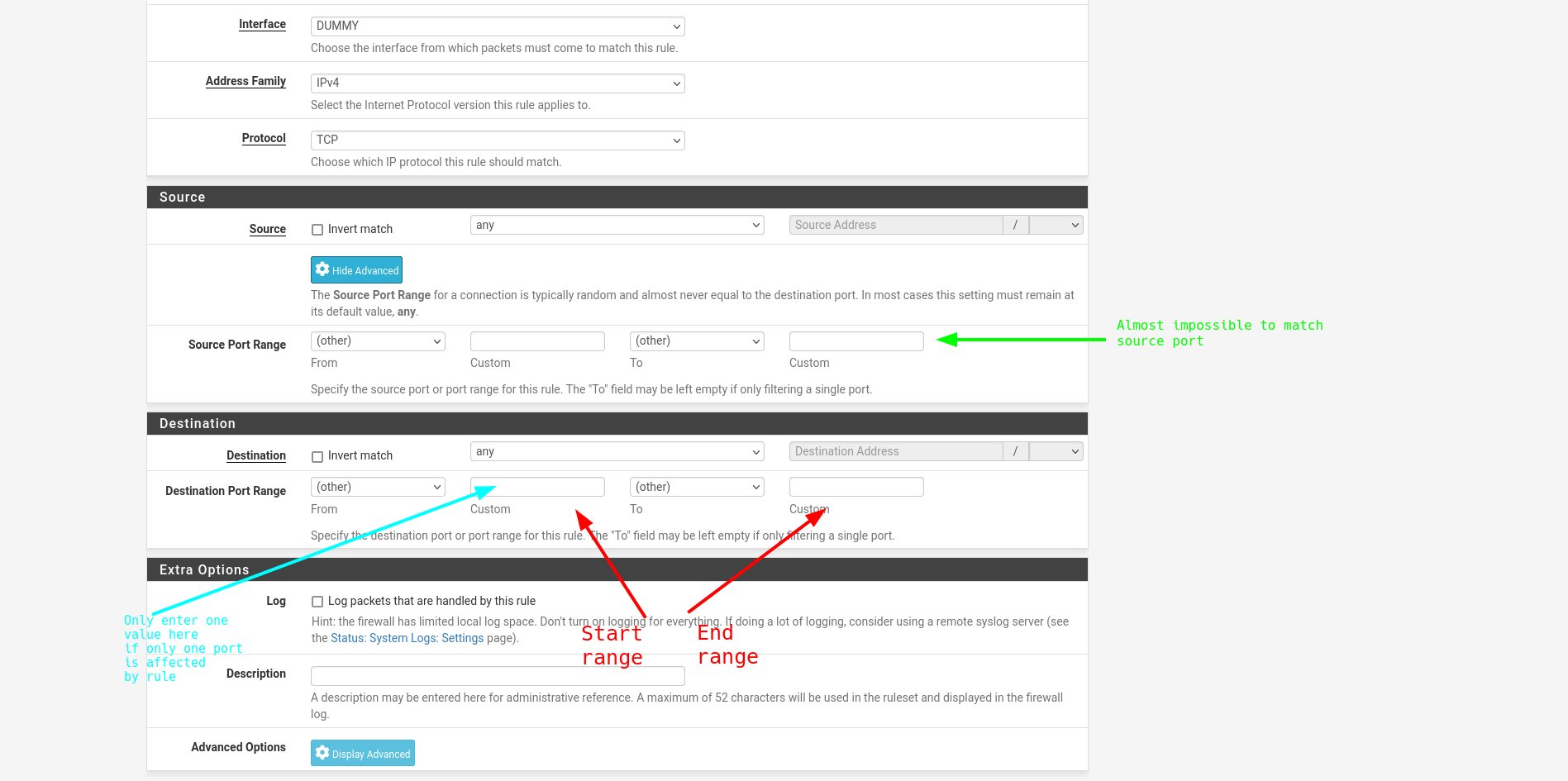
Rule setting
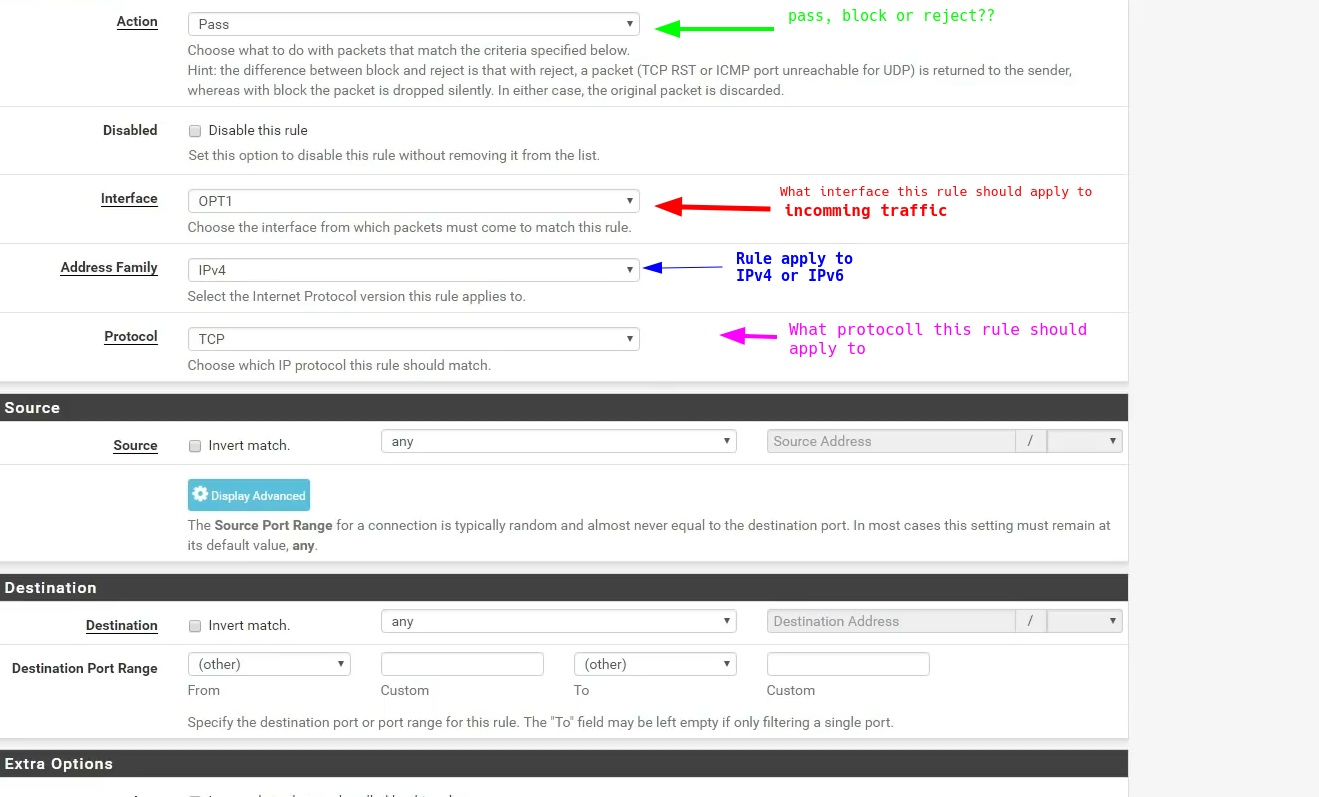
Mapping IP adresses
LAN Address or LAN Net?
In pfSense’s firewall rules, the terms LAN address and LAN net refer to different scopes of the local network. Here’s the difference:
1. LAN Address:
- Meaning: Refers to the specific IP address of the pfSense firewall on the LAN interface.
- Usage: You would use this option when you want to create rules that affect traffic specifically to or from the pfSense device itself on the LAN.
- Example: If your pfSense LAN interface has the IP address 192.168.1.1, then LAN address represents that exact IP. You might use this if you want to allow or block traffic to the firewall (e.g., allowing web interface access via the firewall’s LAN IP).
2. LAN Net:
- Meaning: Refers to the entire subnet that the LAN interface belongs to. This includes all IP addresses in the local network range.
- Usage: You use this option when you want to create rules that apply to all devices within the local network.
- Example: If your LAN is set to the subnet 192.168.1.0/24, then LAN net represents all addresses from 192.168.1.1 to 192.168.1.254. You might use this to allow or block traffic going to or from the entire LAN network, not just the firewall.
Summary of Differences:
- LAN address = The single IP address of pfSense on the LAN interface.
- LAN net = The entire subnet or range of IP addresses on the LAN.
This distinction is important when setting firewall rules, as LAN address targets only the firewall itself, while LAN net targets the broader local network.

