Users and Group
What are Users and Group
In Linux, users represent individual accounts that can log in and interact with the system. Each user has a unique username and user ID (UID) that distinguishes them from other users. Users have personal home directories where they can store their files, and they operate with a specific set of permissions that dictate what files and commands they can access or execute. This separation of user accounts ensures that personal data is kept private and that users can only perform actions permitted by their privileges.
Groups in Linux are collections of users that share common permissions and access rights. Each group has a unique group name and group ID (GID). Groups are used to simplify the management of permissions for multiple users; instead of assigning permissions to each user individually, permissions can be assigned to a group, and all users in that group inherit those permissions. This is particularly useful for managing access to files, directories, and resources in a collaborative environment.
By using users and groups together, Linux systems can maintain a robust and flexible security model. Users can belong to multiple groups, allowing them to have varying levels of access to different resources. Administrators can easily manage user permissions by adjusting group memberships and setting group-specific permissions on files and directories. This system enhances security by enforcing the principle of least privilege, ensuring users only have access to the resources they need for their specific roles.
We will cover here linux cli commands and we will need sudo or root privilegies to run the commands.


How to install packages for managing users and groups
Most linux distros have included all packages as part of the base install of linux.
Termomonlogy and Concept
Here are some basic terminologies and concepts associated with managing users and groups in Linux:
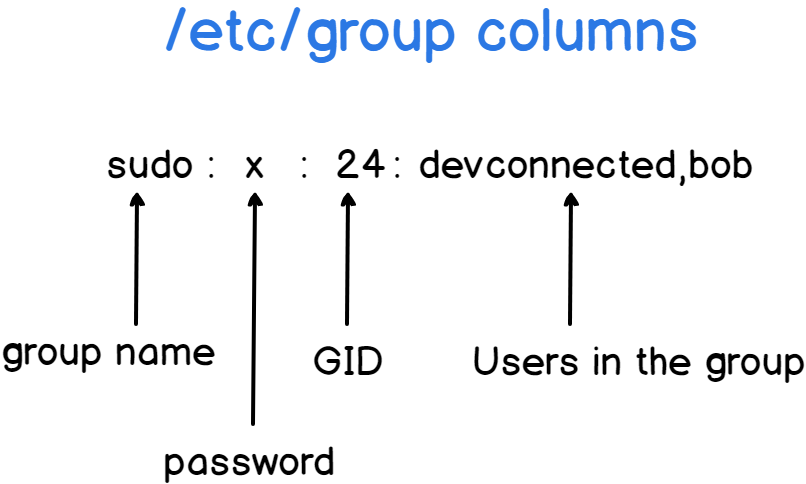
User: An individual account on the Linux system, identified by a unique username and user ID (UID).Group: A collection of users, identified by a group name and group ID (GID), used to manage permissions for multiple users collectively.UID (User ID): A unique numerical identifier assigned to each user on the system.GID (Group ID): A unique numerical identifier assigned to each group on the system.Home Directory: A personal directory for each user where they can store their files, typically located at/home/username.Root User: The superuser account with UID 0, having complete control over the system.Primary Group: The default group assigned to a user when they are created. This group is used for file creation and ownership.Secondary Groups: Additional groups that a user can be a member of, providing additional access rights and permissions./etc/passwd: A file that contains basic information about users, such as username, UID, GID, home directory, and shell./etc/group: A file that contains information about groups, including group names, GIDs, and group memberships./etc/shadow: A file that contains secure user account information, including encrypted passwords and password policies.useradd: A command used to create a new user.usermod: A command used to modify an existing user’s account.userdel: A command used to delete a user account.groupadd: A command used to create a new group.groupmod: A command used to modify an existing group.groupdel: A command used to delete a group.chown: A command used to change the owner and group of files and directories.chmod: A command used to change the permissions of files and directories.passwd: A command used to change a user’s password.sudo: A command that allows a permitted user to execute a command as the superuser or another user.sudoers: A file that specifies which users have permission to use thesudocommand and what commands they can run.ACL (Access Control List): A more flexible permissions system that allows setting permissions for individual users and groups beyond the standard owner/group/others model.NSS (Name Service Switch): A mechanism that provides a variety of sources for common configuration databases and name resolution (e.g.,/etc/passwd, LDAP).PAM (Pluggable Authentication Modules): A framework that integrates multiple low-level authentication schemes into a high-level API for programs.
Understanding these terms and concepts is fundamental for managing users and groups effectively on a Linux system.
Files for storing passwords
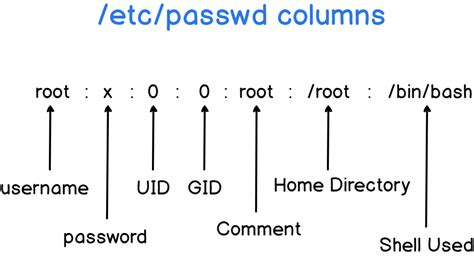
/etc/passwd
UID
User ID
Each user has its own unique id. The first user created at a installation of linux of usually always given the “start number” of 1000 and the next is incremented by one. Theese are used by humans. Usually id lower than 1000 is used by the linux system itself, aka system accounts
GID
Group ID
Each group has its own unique id
/etc/group
Overview Permissions
Commands - Users
Be explicityly, as always in linux, especially when using these command. They may differ from different distrubutuions for what is default
| DESCRIPTION | COMMAND |
|---|---|
|
Create a user "nameofuser" Note, do NOT assume that a home folder for that user was created Usually NOT recommended |
sudo useradd "nameofuser" |
|
Remove the user kallestor Note, do NOT assume that the home folder will also be removed Usually NOT recommended |
sudo userdel kallestor |
|
Create a user foxmulder with a home folder Recommended |
sudo useradd -m foxmulder |
|
Remove the user foxmulder AND the home folder Recommended Ignore the message about mail spool |
sudo userdel -r foxmulder |
|
Set password for currently logged user This is also used for changing the password for the currently logged user |
passwd |
|
Set password for the user foxmulder |
sudo passwd foxmulder |
|
Create system user named godsysuser Usually done for automation Used in combination with cron |
sudo useradd -r godsysuser |
Commands - Misc
| DESCRIPTION | COMMAND |
|---|---|
|
List "real" users not a good ide... |
ls -l /home |
|
List ALL users First column |
cat /etc/passwd |
|
Count ALL users |
cat /etc/passwd | wc -l |
|
Set the default for useradd Each distro is free to choose what is the default |
cat /etc/default/useradd |
Commands - group management
2 kinds of group exist in linux:
Primary groupsSecondary(supplymentary) groups
All groups are the same but the one assigned to a user is called the primary group. You could call the primary group the default one e.i when a user creates a file, by default, the file’s group ownership is set to the user’s primary group.
When a user is added to new group the user need to logout and login in order for the changes to take effect!
| DESCRIPTION | COMMAND |
|---|---|
|
List the all the groups that the currently log user belongs to |
groups |
|
To list all the groups a specific user belongs to |
groups username |
|
To list all availible groups |
getent group OR cat /etc/group |
|
Add a new group named gamers |
sudo groupadd gamers |
|
Delete the group named gamers |
sudo groupdel gamers |
|
Add the user heaton to the group gamers OR |
sudo usermod -aG gamers heaton |
|
Add the user heaton to the group gamers |
sudo gpasswd -a heaton gamers |
|
Remove the user heaton from the group gamers |
sudo gpasswd -d heaton gamers |
|
Change the primary group for the user pelle to katter Usually NOT recommended Not to change some more things also... |
sudo usermod -g katter pelle |
Important Files - Users
Also called the etsy password file
/etc/passwd
Returns a list in format
foxmulder:x:1001:1003:Fox Mulder:/home/foxmulder:/bin/sh
foxmulder = the user
x = the password
1001 = User ID
1003 = Group ID (primary group)
Fox Mulder = User Information Field(Optional)
/home/foxmulder = the home directory
/bin/sh = refers to the shell designated to the user
If there is a “missing field” it only mean that no entry was made. E.i User Information Field is optional.It will be displayed as ::
Also called the etsy shadow file
/etc/shadow
Returns a list in format, that might look like
username:$6$saltsalt$hashedpassword:18552:0:99999:7:::
The fields are:
Username: The user account name (e.g.,username).Password: The hashed password, which might start with a$character followed by a number that indicates the hashing algorithm used. For example:$1$for MD5$2a$for Blowfish$5$for SHA-256$6$for SHA-512- If the password field contains a
*or!, it indicates that the account is locked or has no password.
Last password change (lastchanged): The number of days since January 1, 1970, when the password was last changed (e.g.,18552).Minimum: The minimum number of days required between password changes (e.g.,0means no minimum).Maximum: The maximum number of days the password is valid before the user is required to change it (e.g.,99999).Warn: The number of days before the password expires that the user is warned (e.g.,7).Inactive: The number of days after the password expires before the account is locked (e.g.,-1or empty means this feature is not used).Expire: The number of days since January 1, 1970, after which the account is disabled (e.g., empty means the account does not expire).Reserved: A reserved field for future use, which is usually empty.
Here’s a breakdown of the example:
username: The user’s login name.$6$saltsalt$hashedpassword: The hashed password with SHA-512 algorithm and a salt (saltsalt).18552: The last password change was on day 18552 since the epoch (January 1, 1970).0: No minimum days required between password changes.99999: Password never expires.7: User is warned 7 days before the password expires.-1: The account will never be disabled due to inactivity.: The account does not have an expiration date.: Reserved field, usually empty.
This file is crucial for system security and should be managed carefully, typically only by the root user or through authorized system management tools.
SSH - User and Group - Allow
For Users
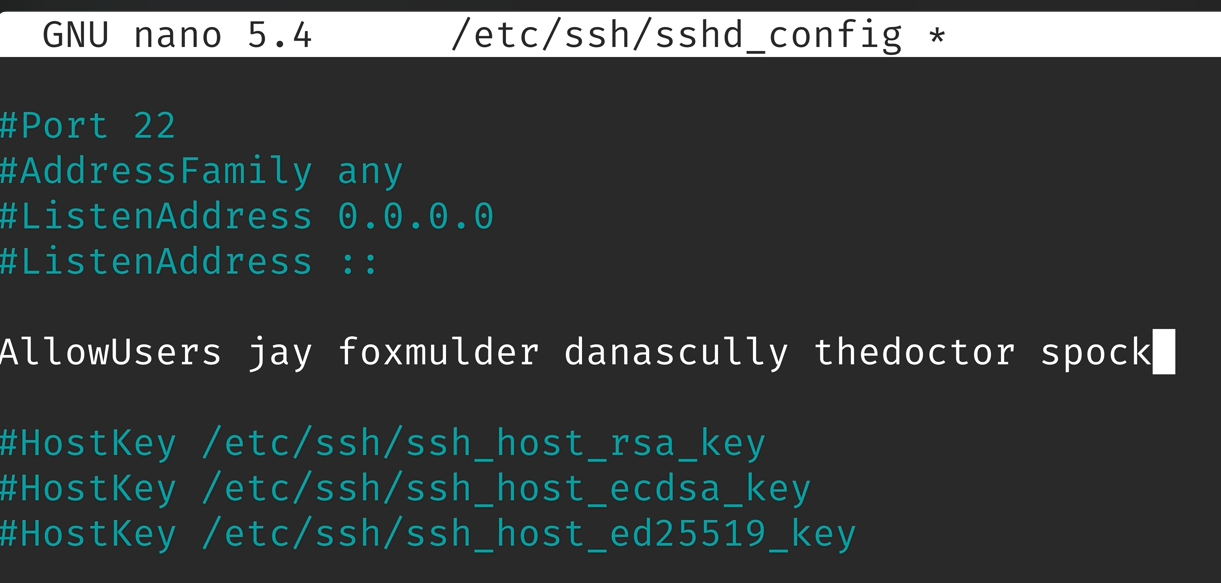
For Groups
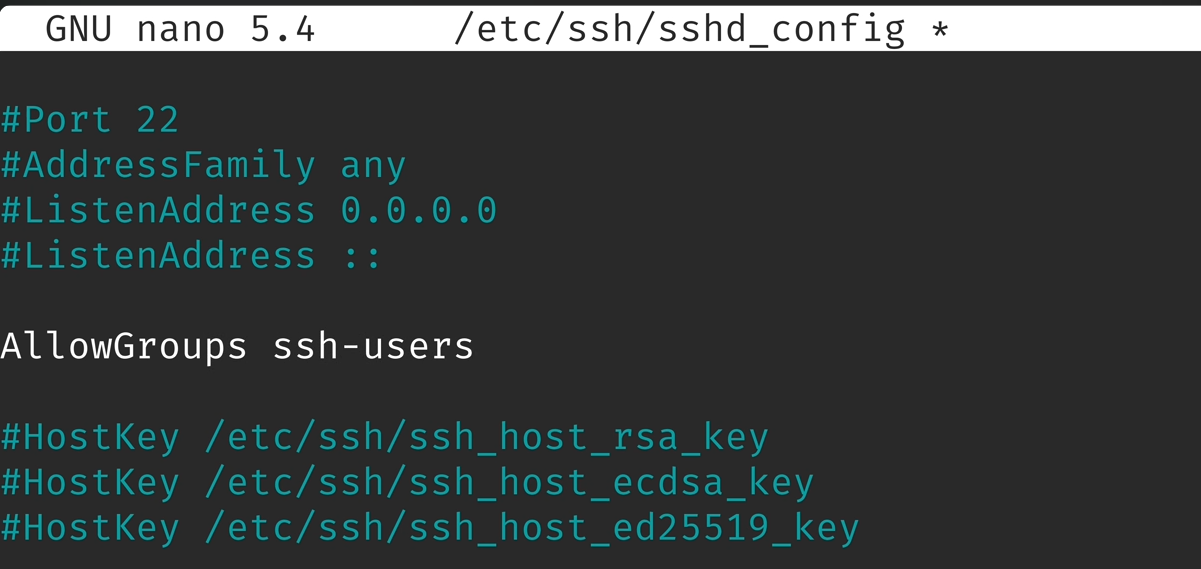
sudo
Elevates normal user to superusers aka root usually.
Note 1: Usually sudo is installed by default else apt install sudo
Note 2: You may first need to swith to root account to install sudo, su - and enter password
Note 3: On some distribution the root account might be locked
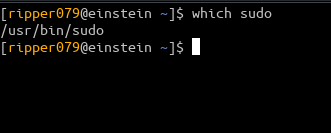
Verify to check if sudo is installed
which sudo
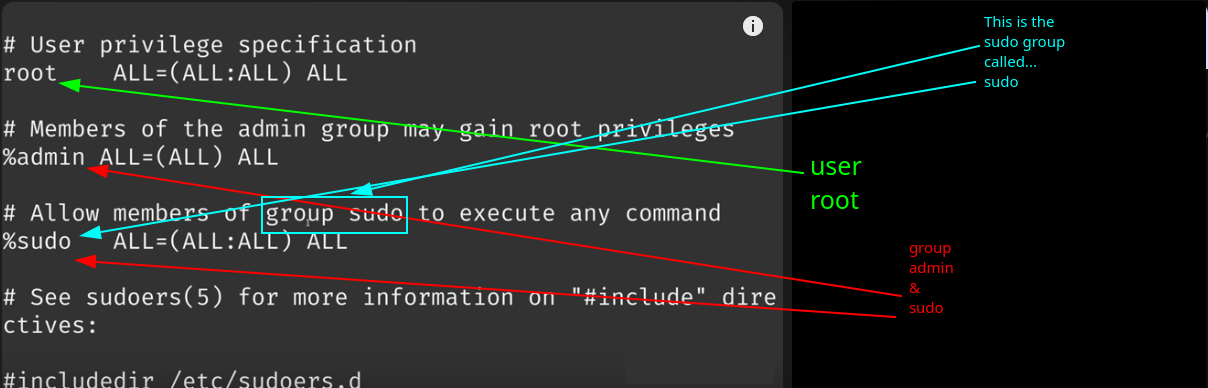
Determine which group sudo belongs to (sudo and wheel are common), this might differ depending distribution. This info is located in the sudo:er file which is located at
/etc/sudoers
Note: You might need to be run as root to do cat /etc/sudoers OR nano /etc/sudoers
Verify that user is a member in the sudo group
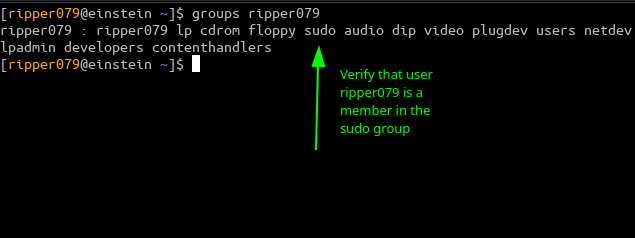
Note:If the user is NOT a member in the sudo group you could added it with usermod -aG sudo ripper079 . In order for this group membership to take affect the user(ripper079) needs to logout and login again
Commands
List what commands you are allowed(and not allowed) to run (currently logged in user)
sudo -l
Edit the /etc/sudoers
NEVER edit the /etc/sudoers directly you actually lock yourself out it the editing is made wrong! You should do it via visudo
sudo visudo
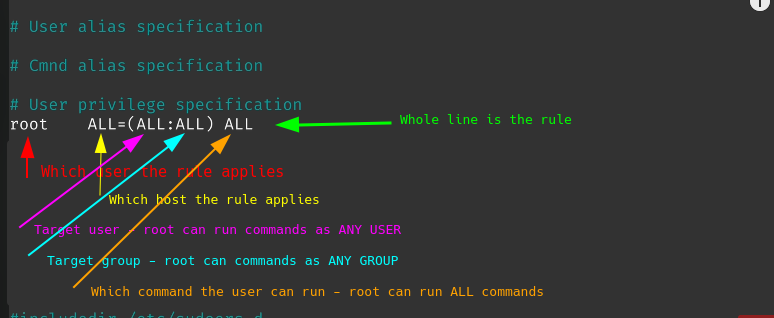
Lets analyse the content of a line in the /etc/sudoers
This one applier to a user, root in this case
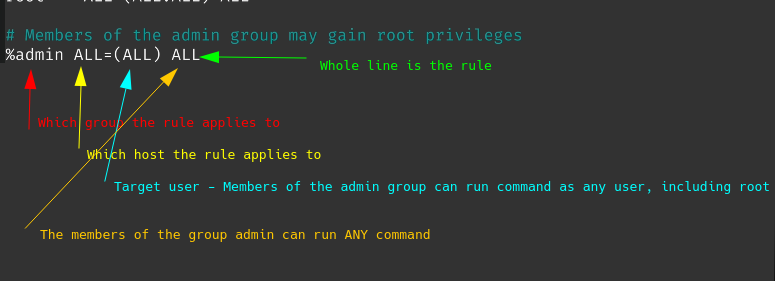
This one applier to a group, admin in this case
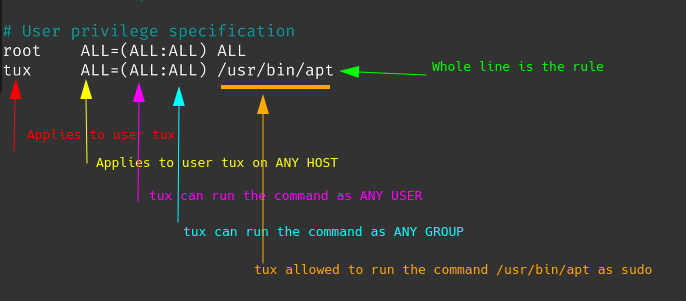
This one applies to a user named tux
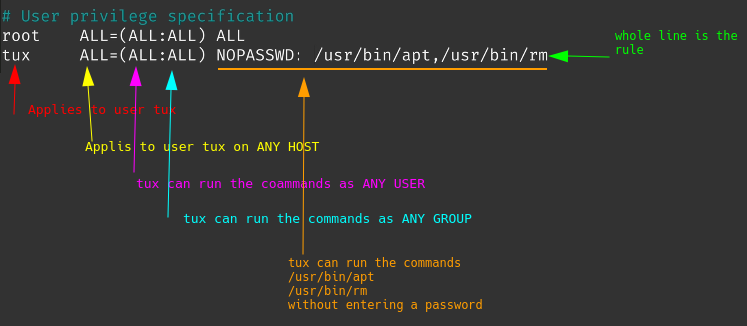
Another one applied to the user tux. No password needed here
one major benefit with /usr/sbin/visudo
You will be presented with “What now?” question….
The option you may pick from are.
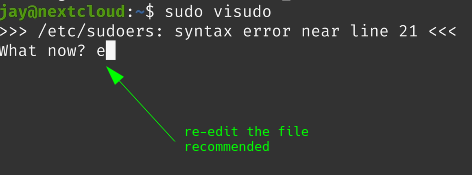
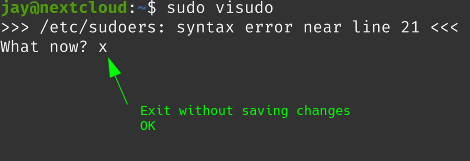
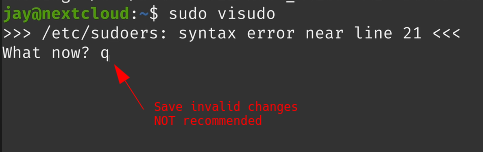
FAQ
1. adduser (Higher-level, Debian-based Utility):
- Script/Wrapper:
adduseris a Perl script that acts as a user-friendly interface foruseradd. - Interactive: It prompts the user for details such as the new user’s password, home directory, full name, and other information in an easy, interactive manner.
- Automatic Setup: It automates common tasks such as creating the home directory, setting default shell, and copying configuration files (e.g.,
.bashrc,.profile) from/etc/skel. - Default Behavior: By default, it also sets up a user-specific group and assigns the user to it.
- Usage:
adduseris primarily used in Debian-based systems (e.g., Ubuntu).
adduser guddaniel
Running this will guide you through the process of setting a password, and it will handle things like home directory creation automatically.
2. useradd (Low-level, Standard Utility):
- Binary:
useraddis a more basic, lower-level command that is available across most Unix-like systems (including Debian, Red Hat, etc.). - Non-Interactive: It requires you to specify all options and parameters explicitly via command-line arguments (e.g., home directory, shell, etc.). It does not prompt for input like
adduser - Minimal automation: By default, it does not automatically create the home directory or set passwords—you must pass additional flags to do so.
- Usage: Because it’s more bare-bones, administrators often use
useraddin scripts where explicit control over user creation is needed.
Key Differences:
| Feature | adduser |
useradd |
|---|---|---|
| Type | Higher-level script | Low-level command |
| Interactivity | Interactive, prompts for inputs | Non-interactive, requires flags |
| Home Directory Creation | Automatic | Must use -m flag |
| Password Setup | Prompts for password | Requires separate passwd command |
| Ease of Use | Easier to use, beginner-friendly | More control, better for scripting |
| Default Behavior | Creates user-specific group, config files | Needs explicit options |
In general, adduser is more convenient for manual user creation,

