UFW - Uncomplicated FireWall
What is ufw


How to install ufw
Install the package
sudo apt install ufw
Verify ufw is is installed
ufw --version
Default setup config to do is
1. Check status for ufw. (should be inactive)
sudo ufw status
2a)Set default policy for incoming traffic
sudo ufw default deny incoming
2b) Set default policy for outgoing traffic
sudo ufw default allow outgoing
2c) The default rules are specificed in the config file
cat /etc/default/ufw
4. Allow ssh traffic. Very important so you do NOT lock your self out
sudo ufw allow ssh
5. Enable ufw
sudo ufw enable
Now only ssh works.
Additional
To enable http and https traffic do
Enable http
sudo ufw allow http
OR
sudo ufw allow 80
Enable https
sudo ufw allow https
OR
sudo ufw allow 443
Enable mysql
sudo ufw allow 3306
Enable ftp
sudo ufw allow ftp
OR
sudo ufw allow 21/tcp
Enable sftp
You only need to allow SSH in order for sftp to work
Termomonlogy and Concept
UFW (Uncomplicated Firewall):A user-friendly interface for managing firewall rules on Linux systems.iptables:The default firewall administration tool for Linux, which UFW abstracts and simplifies.Rule:A configuration directive specifying whether to allow or deny traffic based on certain criteria such as ports, IP addresses, or protocols.Inbound Traffic:Traffic coming into the system from external sources, which can be controlled using UFW rules.Outbound Traffic:Traffic leaving the system to external destinations, also manageable through UFW rules.Port:A numerical identifier associated with a specific network service, such as port 80 for HTTP or port 22 for SSH.Protocol:A set of rules defining how data is transmitted over a network, such as TCP (Transmission Control Protocol) or UDP (User Datagram Protocol).Allow:Permitting specified traffic to pass through the firewall based on defined rules.Deny:Blocking specified traffic from passing through the firewall based on defined rules.Logging:Recording information about traffic matches to UFW rules for monitoring and analysis purposes.Default Policy:The action taken by the firewall for traffic that does not match any explicitly defined rules, usually set to ‘deny’ for inbound traffic and ‘allow’ for outbound traffic.
ufw - cli general
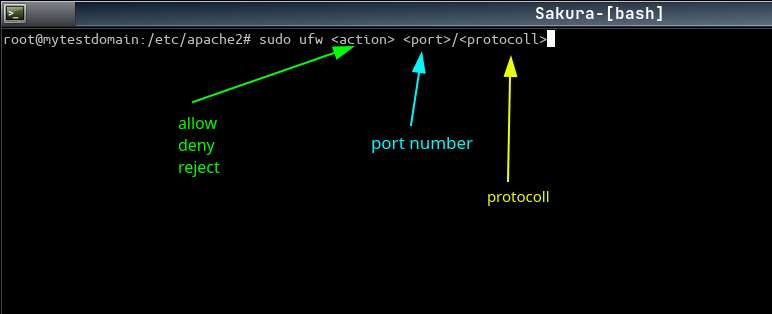
ufw - cli specific
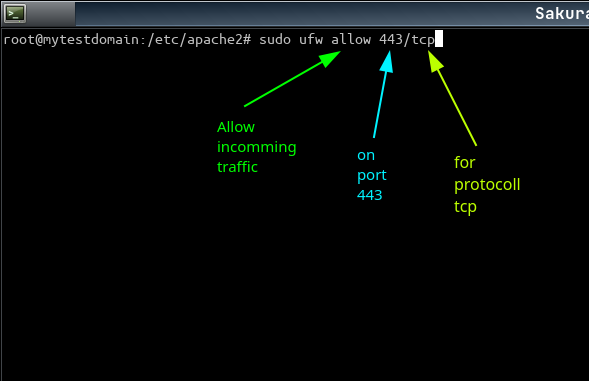
List of protocol
tcpudpicmpall(allows all protocolls)
If not specifying a protocoll then tcp is the default
Commands - Managing ufw
| DESCRIPTION | COMMAND |
|---|---|
| Status of ufw | sudo ufw status |
| Enable ufw | sudo ufw enable |
| disable ufw | sudo ufw disable |
| Reload rules for ufw | sudo ufw reload |
| Reset configuration to default settings | sudo ufw reset |
Commands - Rules (directive) settings - ufw
sudo ufw disable && sudo ufw enable
| DESCRIPTION | COMMAND |
|---|---|
|
configures the default policy for all incomming traffic o deny all incoming connections |
sudo ufw default deny incoming |
|
configures the default outgoing policy to allow all outgoing traffic |
sudo ufw default allow outgoing |
|
Adds a rule Allow incoming traffic on port 80 |
sudo ufw allow 80 |
|
Adds a rule Allows incoming traffic from the IP address 10.0.0.1 to any port and protocol. |
sudo ufw allow from 10.0.0.1 |
|
Adds a rule Allow incomming TCP traffic on port 22 Important so you do NOT get locked out (openSSH rule) |
sudo ufw allow 22/tcp |
|
Adds a rule in port ranges Allow incomming TCP traffic on port 60 to 80 |
sudo ufw allow 60:80/tcp |
|
Adds a rule with service names (Get the service name from previous command output. No need to specify port number and protocol) |
sudo ufw allow http |
|
Adds a rule to allow incmoing TCP traffic from IP address 14.56.12.34 on port 22 (Allow ssh access from ONLY ip address 14.56.12.34) IMPORTANT!!! |
sudo ufw allow from 14.56.12.34 to any port 22 proto tcp |
|
Adds a rule to allow incomming traffic from IP address 14.56.12.34 on port 22 (Variation of previous command) IMPORTANT!!! |
sudo ufw allow from 14.56.12.34 to any port 22 |
|
Get a list of service name(s) The profiles are stored in /etc/ufw/applications.d/ |
sudo ufw app list |
|
Current status of UFW rules in a numbered listformat |
sudo ufw status numbered |
|
Remove rule number 6 (Get the number from the previous command) |
sudo ufw delete 6 |
Commands - misc
| DESCRIPTION | COMMAND |
|---|---|
| Status of ufw | systemctl status ufw |
|
View a system file containing mappings of port numbers to service names |
less /etc/services |
Dummy examples (Not commonly used)
To be absolutely sure you could run (overkill)
sudo ufw disable && sudo ufw enable
| DESCRIPTION | COMMAND |
|---|---|
|
Allow Incoming SSH Traffic Allow incoming SSH traffic (port 22) The in the default... |
sudo ufw allow in ssh |
|
Allow Outgoing HTTP(port 80) |
sudo ufw allow out http |
|
Allow Outgoing HTTPS(port 443) |
sudo ufw allow out https |
|
Deny Incoming Traffic on Specific Port Deny incoming traffic on a specific port (for example, port 1234) |
sudo ufw deny in 1234 |
|
Deny Outgoing Traffic to Specific IP Address Deny outgoing traffic to a specific IP address (for example, 192.168.1.100) |
sudo ufw deny out to 192.168.1.100 |
|
To allow incoming traffic from a specific IP address, port number, and protocol using UFW, |
sudo ufw allow from [IP address] to any port [port] proto [protocol] |
|
Allow incoming TCP traffic from IP address 192.168.1.100 on port 1234 |
sudo ufw allow from 192.168.1.100 to any port 1234 proto tcp |
|
Adds a rule to allow incomming traffic from IP address 14.56.12.34 on subnet 24 on port 22 |
sudo ufw allow from 14.56.12.34/24 to any port 22 |
General info
You can add rules even if the ufw is not enabled
Restart ufw with sudo ufw restart when
- After a System Update
- Configuration Changes
- To Clear Issues
- Service Management
Reload ufw with sudo ufw reload when
- Updating Configuration Files
- After Changing Default Policies
- When Modifying Application Profiles
- To Refresh the Firewall Rules
- Does not disable the firewall
Enable ufw with sudo ufw enable when
- Turn on ufw
Disable ufw with sudo ufw disable when
- Turn off ufw
- Do NOT change or modify existing rules
FAQ
Numerous site for this
Well-Known Ports (0-1023)
- 20 – FTP (File Transfer Protocol) Data Transfer
- 21 – FTP (File Transfer Protocol) Command Control
- 22 – SSH (Secure Shell)
- 23 – Telnet (Unencrypted remote login service)
- 25 – SMTP (Simple Mail Transfer Protocol)
- 53 – DNS (Domain Name System)
- 67 – DHCP (Dynamic Host Configuration Protocol) Server
- 68 – DHCP (Dynamic Host Configuration Protocol) Client
- 80 – HTTP (HyperText Transfer Protocol)
- 110 – POP3 (Post Office Protocol version 3)
- 119 – NNTP (Network News Transfer Protocol)
- 123 – NTP (Network Time Protocol)
- 143 – IMAP (Internet Message Access Protocol)
- 161 – SNMP (Simple Network Management Protocol)
- 194 – IRC (Internet Relay Chat)
- 443 – HTTPS (HyperText Transfer Protocol Secure)
- 445 – SMB (Server Message Block)
- 465 – SMTPS (Simple Mail Transfer Protocol Secure)
- 514 – Syslog (System Logging Protocol)
- 636 – LDAPS (LDAP over SSL)
- 990 – FTPS (File Transfer Protocol Secure – Implicit mode)
Registered Ports (1024-49151)
- 1433 – Microsoft SQL Server
- 1434 – Microsoft SQL Monitor
- 2049 – NFS (Network File System)
- 3260 – iscsi
- 3306 – MySQL
- 3389 – RDP (Remote Desktop Protocol)
- 5432 – PostgreSQL
- 5900 – VNC (Virtual Network Computing)
- 6379 – Redis
- 8080 – HTTP Alternate
- 8443 – HTTPS Alternate
Dynamic or Private Ports (49152-65535)
- These ports are usually used for temporary or private services and are often assigned dynamically by the system when needed.
- Incoming Rules: Focus on what external traffic is allowed to access your
- Outgoing Rules: Control what traffic is allowed to leave your server.
- Defaults: It’s common to set defaults to deny incoming traffic while allowing outgoing traffic, as this aligns with typical security best practices.

